Before we begin,
If you’re not yet familiar with the problem that Whitelists aim to solve in Cyber Security Awareness, I recommend you read the following articles:
- Do You Really Know What Phishing Simulation Is? Sure?
- Quick Checklist for Creating Your First Phishing Campaign ~ SMARTFENSE Blog
What is Direct Message Injection?
Direct Message Injection (DMI) is a phishing simulation delivery technique that we can use within our organizations.
This method allows for direct injection of emails into the inbox of our organization’s users, typically leveraging an API developed by our email service provider.
Thus, our phishing simulation tool doesn’t need to bypass all the organization’s security tools to reach the end user’s inbox:

Instead, the email can be inserted directly into the inbox, achieving something like this:
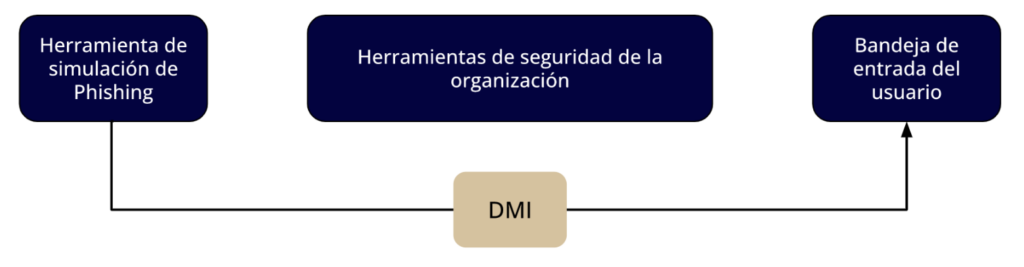
This simulation delivery method often simplifies the Whitelisting process or even eliminates the need for it. This is because DMI bypasses most of the organization’s email filtering rules and tools.
Can We Forget About Whitelists?
The answer largely depends on the technologies used in our organization.
Primarily, we need to consider the following: Post-delivery inbox filtering can interfere with email delivery even when inserted via DMI, so if we have such a tool, we’ll need to configure Whitelists in it.
Also, let’s not forget that Whitelists are divided into two parts:
- Whitelist for proper email reception.
- Whitelist for safe browsing of simulated phishing sites.
DMI assists only in the first point.

Conclusions
Direct Message Injection is a delivery method that can save us a lot of headaches for various reasons.
One example is that many CISOs are unaware of the protection technologies implemented in their organization, which makes it difficult to accurately measure user behavior.
With DMI, the process is simpler and requires less knowledge of the organization’s security infrastructure.
Another significant headache to mention is that protection tools often update and can unexpectedly disrupt a good Whitelist.
With DMI, we reduce or even eliminate the tools involved in our Whitelist for proper email reception.
Therefore, with DMI, the likelihood of such scenarios decreases. While this method doesn’t eliminate the need for a Whitelisting process, it certainly reduces it and allows us to measure user behaviors more quickly, which is ultimately our goal when simulating phishing attacks.


Leave a Reply