About Smishing
Is it really necessary to explain it?
Smishing is that old acquaintance of cybersecurity that we have all come across at one time or another. Who hasn’t read a post about smishing, a statistic, a news item?
The objective of Smishing is identical to that of Phishing and can be generalized into two main groups:
- Stealing confidential information
- To install malicious software
The only difference is the medium: it is not an email, but an SMS.
An SMS… Does anyone use SMS in the year 2024?
Personally, I haven’t used SMS for almost a decade, except to validate my mobile number when registering on a website.

And for this reason I honestly didn’t think Smishing could be a big deal. Compared to the massive use of email, how much damage could Smishing be doing in today’s world?
And yes, it was a very innocent guess. It turns out that Smishing is the main gateway for threats in the mobile world. Credential theft, malware installation, scams, extortion… In short: all the usual cybercrimes, adapted to start with a text message.
Advantages of sending Smishing
Mobile is generally the least protected communication channel of all. Compared to sending an email, an SMS spares the cybercriminal many, if not all, corporate security barriers. As an extra advantage, it is usually a means of direct contact with the victim.
On the other hand, it is a medium that does not receive enough attention in awareness programs. Perhaps partly because it is overshadowed by other topics such as Phishing and Ransomware, or also because the rules for determining whether an SMS is secure are not as clear as when it comes to analyzing an email.
Finally, this medium favors the use of various social engineering scenarios that might not make as much sense via email, such as stealing a user’s 2FA, for example.
In the end, for now it’s all advantages… If I were a cybercriminal, I think I would send Smishing.
Anatomy of a Smishing
Sender of the SMS
Like Phishing, this is a message that impersonates the identity of a person or company.
It is possible to impersonate the sender of an SMS. However, the result of the different spoofing techniques will depend a lot on the carrier involved in sending the message.
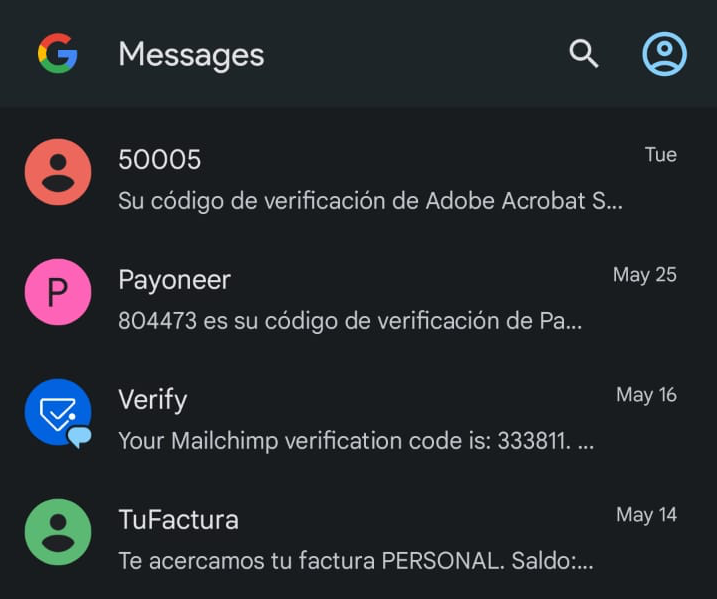
Generally, if spoofing fails, the SMS is still delivered. The only difference is that instead of the spoofed sender, a generic number such as “50005” arrives.
Is this a disadvantage? I don’t think so… Let’s think about it: how do we determine if the sender of an SMS is trustworthy? I invite you to open the list of SMS received on your cell phone. Even those that we know are official, may come from numbers or senders that do not say anything, such as “50005”, “YourBill”, etc. What good practices apply in this case?
The content of the SMS
By definition, SMS are very short messages. It is almost like thinking about Phishing. The objective is the same: through a certain pretext, the aim is to trick the victim into taking a certain action.
Depending on the creativity of the cybercriminal and the degree of personalization of the SMS – often achieved through an OSINT process – the probability of success of the trap will vary.
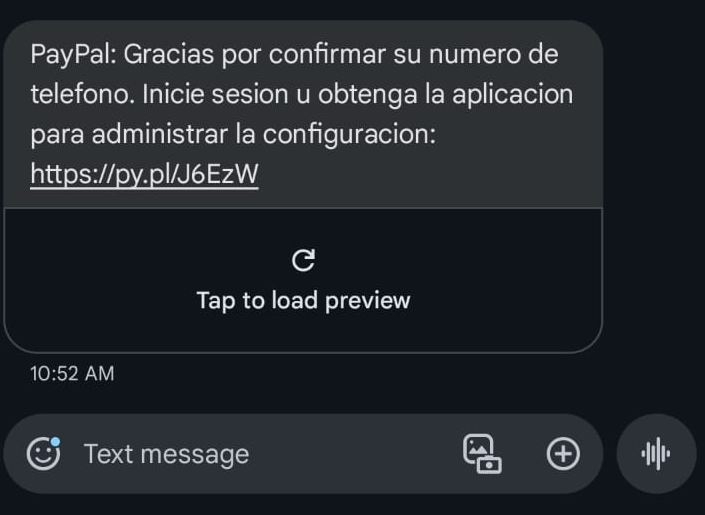
A very common example is SMS messages such as: “Your Microsoft account has detected suspicious activity. Verify your identity here: [link]”.
And here we introduce one of the most relevant issues of this attack:
Shortened links
SMS links (Smishing or not) are usually shortened. This is a widespread custom and is related to the cost of sending an SMS. The more characters the message has, the more expensive it is to send.
This represents a direct advantage for cybercriminals: people are used to receiving shortened links by SMS and usually have no easy way to validate whether the URL to which they are directed is safe or not. This considerably increases the probability of opening links compared to a phishing email.
SMS Delivery
Smishing can be sent using various techniques and tools. Depending on the cybercriminal’s objectives, one or the other will be used.
For example, if the objective is to send a massive attack, there are devices called SIM Farms where it is possible to connect many SIM cards and use them to send SMS:

With such a device, criminals often rotate SIM cards to avoid detection and blocking. In addition, they use SIM cards from providers that offer unlimited SMS plans, which improves the cost/benefit ratio of the attack.
For more customized traps, possibly consider hiring a phishing-as-a-service platform, where the necessary tools for accurate and effective delivery are already provided. There are many options and they usually do not require a large investment.
In cases where the attack is targeted at a specific person and you want to maximize the chances of success, criminals implement complementary techniques such as SIM swapping and SIM duplication.
This is just a brief overview of SMS delivery, as it is a very broad topic.
Theft of 2FA by Smishing
To close, let’s look at a very common case in the world of Smishing: accessing accounts protected with 2FA:
| Cybercriminal | Victim |
| Sends a Smishing message to the victim. Usually the message is going to alert the victim about suspicious activity on their account: Your account has been compromised. Click on this link to verify your identity: [link]. | |
Clicks on the Smishing link and is directed to a Phishing page. You enter your credentials on the Phishing page. Displays on screen the form to enter the verification code sent by SMS. | |
| Receives the credentials the user entered. Enters those credentials on the real site. The real site sends an SMS to the victim with the 2FA code. | |
| Enter the code received on the phishing site. | |
| Enter the code sent by the victim on the real site. Gets access to the victim’s account. |

Final thoughts
Writing this article helped me understand the relevance of Smishing and I hope it has the same effect on the people who read it.
Since I don’t use this type of messages frequently, I incorrectly assumed that it was something little used and of low importance.
But nothing could be further from the truth. Smishing attacks are becoming more and more frequent. They are the main gateway for attacks in the mobile world and users are poorly prepared to identify them.
In SMS, it is customary to have unknown senders and shortened links. This is the perfect recipe for a successful social engineering attack.
In this context, it is particularly important to carry out Smishing simulations to measure the current situation of the people who are part of our organization and also to make them aware of this type of attack:
- are aware of this type of attack
- have tools and procedures to detect them
- help the organization and the community by reporting them.


Leave a Reply